如何使用Filter过滤请求中的SQL注入攻击
1、首先,在项目中新建一个Filter类
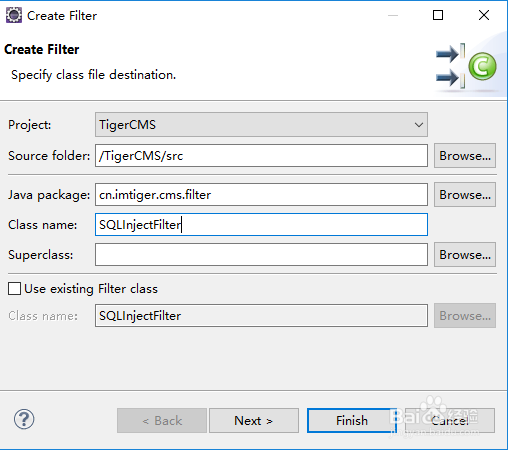
2、将过滤条件配置为过滤全部请求(可以在web.xml中修改)
<filter>
<display-name>SQLInjectFilter</display-name>
<filter-name>SQLInjectFilter</filter-name>
<filter-class>cn.imtiger.cms.filter.SQLInjectFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>SQLInjectFilter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
3、在doFilter方法中编写判断逻辑
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws IOException, ServletException {
//获取请求对象中的参数名称
Enumeration enu = request.getParameterNames();
//遍历枚举
while (enu.hasMoreElements()) {
//取参数名
String paraName = (String)enu.nextElement();
//取参数值并校验
if (isSqlInject(request.getParameter(paraName))) {
return;
}
}
//校验完毕,放行
chain.doFilter(request, response);
}
4、编写SQL注入关键词过滤方法
private static boolean isSqlInject(String injectStr) {
String injStr = "'|and|exec|create|insert|select|delete|update|count|*|%|chr|mid|master|truncate|drop|char|declare|;|or|-|+|,";
String injStrArr[] = injStr.split("\\|");
injectStr = injectStr.toLowerCase();
for (int i = 0; i < injStrArr.length; i++) {
if (injectStr.indexOf(injStrArr[i]) >= 0) {
return true;
}
}
return false;
}